Cold Boot Attack: How to Protect a Computer From being Attacked?
What is a cold boot attack? What does a cold boot do? How can I prevent my computer from the cold boot attack?
These questions popped up in your mind, and you felt at a loss to deal with them. "What should I do?" You ask yourself. Don't worry, to help you understand the cold boot attack and get to know the methods to prevent this attack on your computer system, all the required details are included in this article.
The following article contains the important information about Cold Boot Attacks you need to know, as well as the list of tips to protect your system and its data from hackers, as soon as you have read this article.
Content Navigation
Part 1: Attention: Get to Know Cold Boot Attack
1. What is Cold Boot Attack?
This is the most common question asked by computer users on various technology forum sites. Cold Boot Attack is also known as a side channel attack to steal your computer's sensitive information or we can say data.
It's a process of getting unauthorized access to your computer's data without your knowledge. When you turn off your computer, the data remain as it is in RAM. The RAM of your computer system stores all types of files, data, encryption keys, etc.
After shutting down your system, the recently opened files by the user will be saved in the RAM. Attackers with physical access to your computer could use the technique called Cold Boot Attack to steal your sensitive data.
2. How Does Cold Boot Attack Affect Your Computer?
Cold Boot Attack has been in the market since 2008. Recently, F-Secure has released a report that says nearly all computer systems are vulnerable to cold boot attacks. It includes all the latest computers with the latest processors and advanced features.
The team has found a vulnerable activity that lets attackers have access to your locked system or the system that has been shut down by you recently. The report further says hackers use a physical device to disable overwriting of the data.

The same device can be used to enable the booting of the computer system right from the external devices. Attackers use a USB stick to accomplish this. Without USB access, attackers can't steal the data stored in your computer's RAM. The team has contacted all the major computer manufacturers across the globe and discussed this vulnerability called the cold boot attack.
Moreover, they have stated that the attacks can't be stopped immediately. They have suggested giant firms face the cold boot attacks as it has become more powerful. The F-Secure team has recommended everyone shut down their computer system completely and never put it on sleep mode. This is the common practice to prevent this attack.
Microsoft, Intel, and Apple have already begun working on their end to prevent this attack on their system. They too have confirmed this attack on the latest computer systems which is quite worrisome.
Part 2: How Can You Protect Computer from Cold Boot Attack?
Thankfully, there are several methods by which you can try to protect your computer system from this Cold Boot Attack. Let's get on to the methods now!
Method 1: Disable Sleep Capabilities
You can disable the sleep function on your computer system to protect the system from this attack. This is the simplest way which everyone should do. Your computer system sleeps automatically after 15 minutes or so.

What you need to do here is just disable this function so that your system will never go into sleep mode. This can prevent it from Cold Boot Attack. Let's see how to disable sleep capabilities on a Windows system.
Follow the steps below:
- Click the Start Button on your Windows Computer. The Start button is given at the lower-left corner.
- Click the Settings icon from the Start Menu.
- From the Windows Settings menu, select the System option.
- From the Left Sidebar, select the Power & Sleep option.
- You could see drop-down menus under the Sleep option. Select the drop-down menus one by one and choose the Never option. This option will disable the system from sleeping automatically.
Method 2: Enabling Hibernate Mode
Hibernation is a good option for those who work on the computer system for long hours. Instead of shutting down your system completely or putting it to sleep mode, you should practice choosing the hibernate option. This option helps you boot the system faster and also prevents it from Cold Boot Attack. Let's see how you can enable this option on a Windows system.
Follow the steps below:
- Click the Start Menu from the lower-left corner of your computer system.
- From the given Start Menu, right-click on to the Command Prompt. Select the Command Prompt Admin option as you are going to make some changes to the system.
- Command Prompt Window will be presented to you on your computer's screen. You need to type in the following command in the command prompt window: powercfg.exe /hibernate On
- Press the Enter key after you finish typing the command.
- Close down the command prompt window by clicking on the X button.
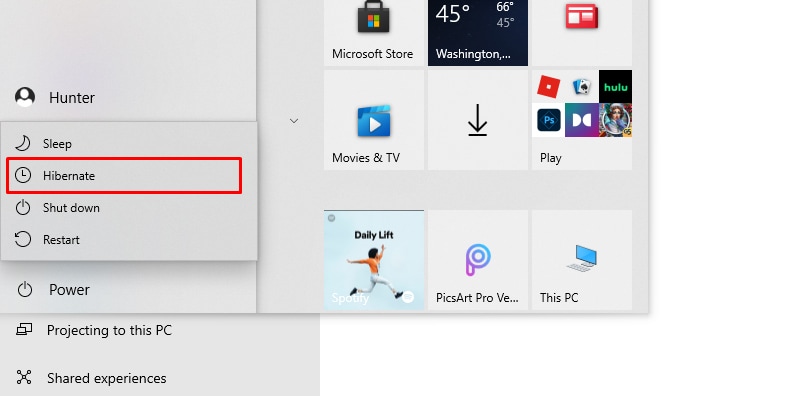
- To check whether the Hibernate option is enabled, just select the Start Menu and then choose the Shutdown or sign out option.
- You could see the Hibernate option right there on the Menu. Always choose the Hibernate option before you leave your computer system.
Method 3: Implementing Security Solutions
Did you know you can add an extra layer of security to your computer system with Bitlocker PIN? Even if you have enabled the Bitlocker option to secure your system, by implementing security solutions through Bitlocker PIN, you can make it more secure with an extra security layer.
By enabling the Bitlocker PIN option, you will be asked to enter the Bitlocker PIN to have access to your computer system. The Bitlocker PIN is completely different from the Admin password that you need to enter to turn on your system.
This PIN prevents the encryption key from automatically loading to the RAM. This prevents your system from Cold Boot Attacks. It is a very effective and
Follow the steps below:
- You have to enable the Bitlocker on your Windows system first. (This option is available only on Windows Professional and Enterprise editions. If you are using Windows Home Operating System, then you won't be able to use this security feature.)
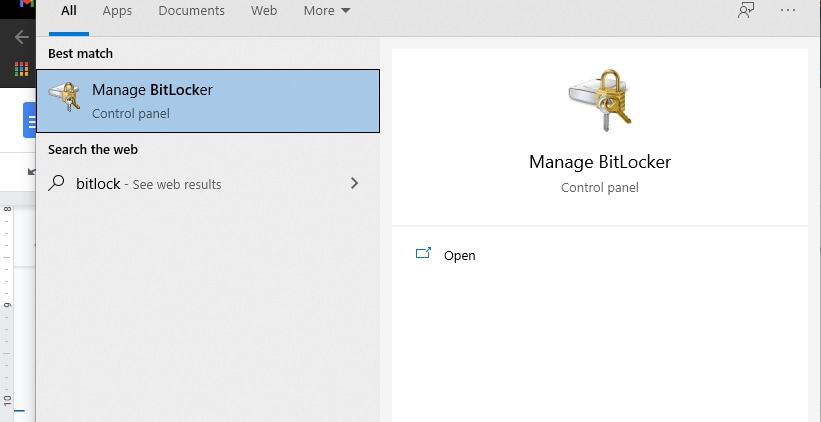
- Now, open Group Policy Settings. Press the Windows + R Keys to open the Run command and type in gpedit.msc, press the Enter button.
- Local Group Policy Editor folder will be presented. From here, you need to select the Bitlocker Drive Encryption option and then click on the "Require Additional Authentication at Startup".
- From this Window, select the Enabled option. Go to the Confirm TPM Startup PIN option and then select Require Startup PIN with TPM option.
- Now, launch Command Prompt on your Windows and enter the following command there: manage-bde -protectors -add c: -TPMAndPIN
- In the command prompt window, you will be asked to enter the Bitlocker's PIN here.
- Once you are done with it, you can close down the Command Prompt Window by pressing the X button.
Extra Tip: How to Recover Lost Data Caused by Cold Boot Attack?
If you have found that your Computer System got attacked with Cold Boot, then chances of losing your important data may be high. If you have lost your important data stored in a system or on an external drive, you can easily restore the lost data using a third-party tool called Recoverit.
The following steps would help you know about how you can recover lost or accidentally deleted data from your computer's hard drive or any other external devices using the Recoverit tool.
First, download and install the Wondershare Recoverit software on a respective PC system. The software is available for both Windows and Mac PC systems.
Step 1:Once the tool is installed, launch it by clicking on its icon.
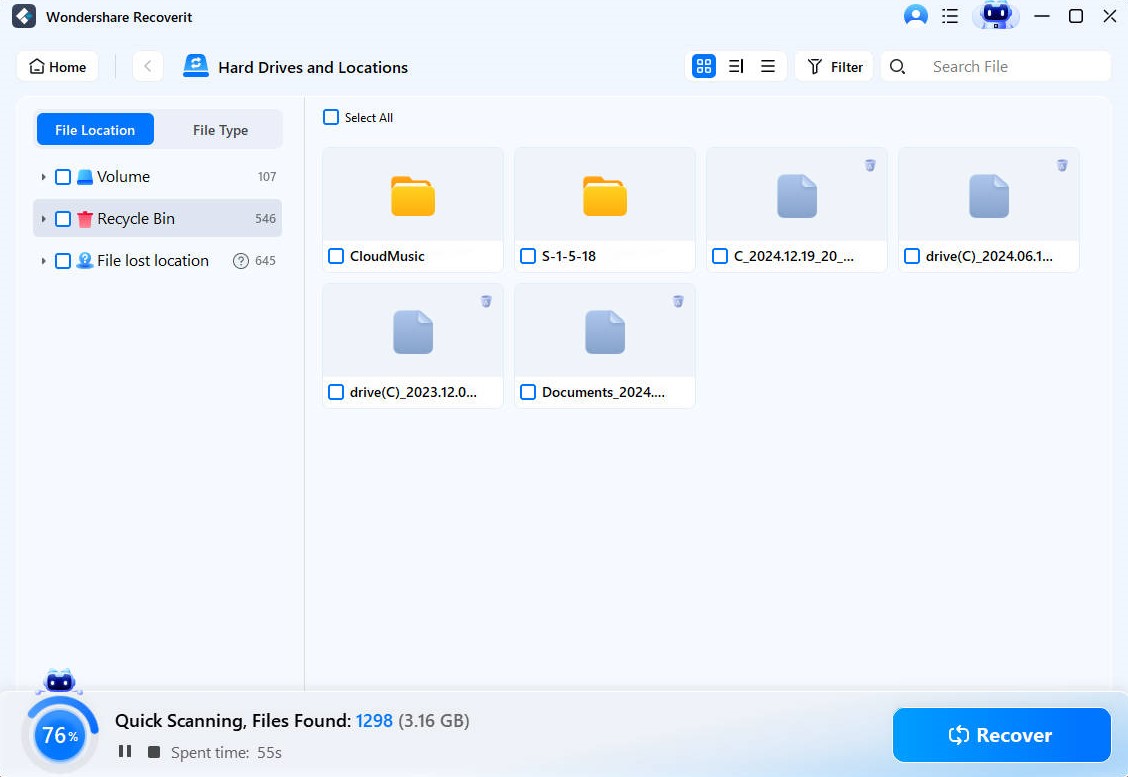
Step 2:If you have connected external drives, then you could see the connected external drives also on the homepage of this software. Now, select the location to start searching for the lost or deleted file. Select the drive from this page and click the Start button.

Step 3:The recovering process of your data will begin itself. You could see the progress of it on your screen.
Step 4:Just select the files you want to recover from this page and click the Recover button.
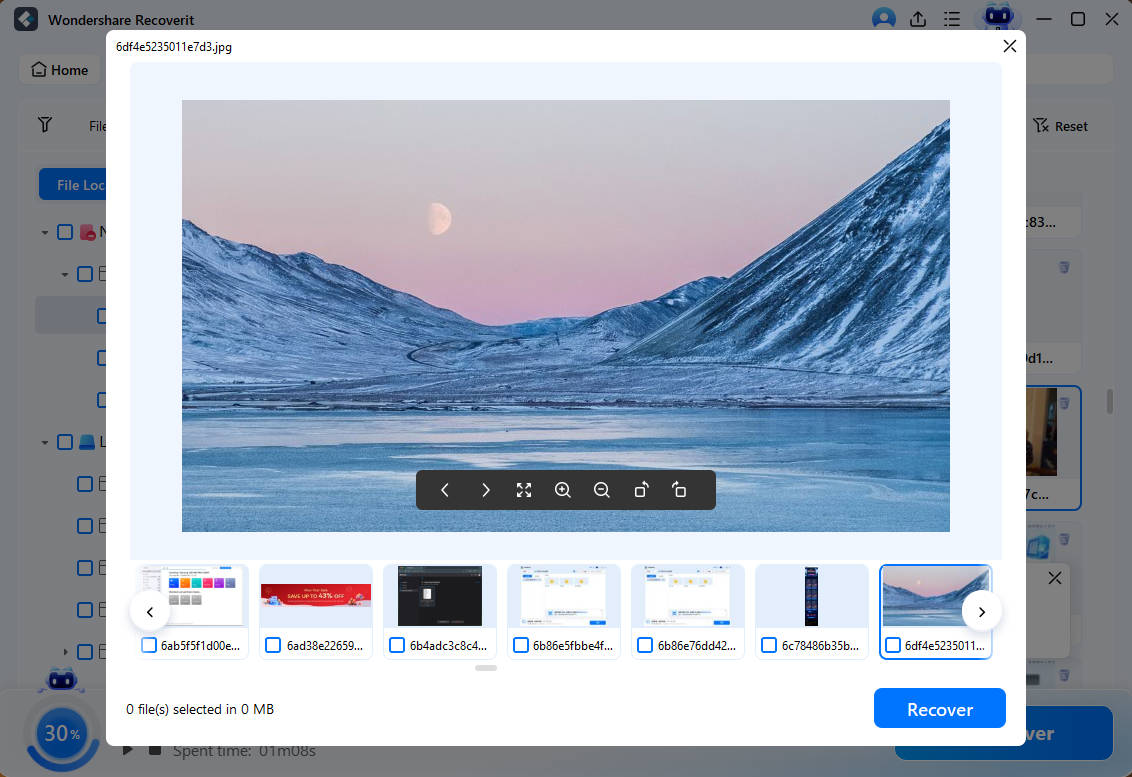
This is how you can easily recover lost or deleted files from your computer's hard drive or external drives using the Recoverit tool.
Choose a location to restore your recovered data, then you have finished the whole recovery process!
Conclusion:
Cold Boot Attack is a serious threat to your computer's sensitive information. If you make online transactions or have stored sensitive information on your system, then you must take proper precautions to protect your system from this attack.
For any type of data-loss issue or accidental deletion of your important data, we would recommend Wondershare Recoverit Data Recovery Tool. It is the most reliable and very useful data recovery tool with full customization. Just download it below, and give it a shot!
Computer Troubleshooting
- Win System Crash
- Windows Tips
- Computer Problems
- Blue Screen Errors














Theo Lucia
chief Editor