Alert USB Drop Attack! Don't Fall into This Trap
Do you know what is USB drop attack? Imagine that, you are walking on the street, and suddenly you find a USB flash drive which looks very new and pretty. Will you pick it up and insert into your PC to see what's inside?
Maybe your answer is yes, because many people will be curious about a seemingly mysterious item. Well, if you do so, then you are stepping into a huge trap!
You all know what a USB drive is, but what you may not realize is that, it can easily be used to launch data attacks against its unsuspecting user, allowing cybercriminals full access to your system. This is why you do not willy nilly plug just any Flash drive you find into your computer system.
To figure out what is USB drop attack, this article will help you in understanding USB drop attack and tell you what to do when your data lost due to the drop attack.
Part 1: How Much Do You Know About USB Drop Attack?
One day the US pentagon military cannot easily forget is the day they experienced a USB drop attack In November 2008. It was regarded by tabloids as the day "The Worm ate the Pentagon". It's one of the most serious breach's ever discovered on the Pentagon's classified systems. This breach was introduced to the system via an unsecured USB drive carrying a worm called Agent.btz. This drive was inserted into one of their systems and the warm crawled straight through their DoD's Network protocols, leaving U.S. government's top intel agencies compromised.
No one knows till this day who created the bug, who was patient zero, if or when any information was taken. It was also discovered that all USB drives confiscated from active operatives already had the bug, but it took a whole of 14 months to completely eradicate the bug.

It took just a flash drive infected with a "agent.btz" virus, inserted into a DoD's computer network to hold the US military ransom. The virus spread quickly throughout their network system, infecting classified and unclassified data alike. This bug opened the door of the US military servers to it's creator, so Top secrete file and information could be transferred else where. In the end, the US military learnt valuable lessons, took step's as well as set-up polices and protocols to prevent re-occurrence of such an attack. They resolved to barn the use of USB drives within the Pentagon and other Defence structures.
Now you have read this story, so what's the definition of USB drop attack? A USB drop attack occurs just as easily as plugging suspicious USB drives, left around by cyber criminals for people to find directly in to your PCs and computers. These mysterious USB's usually contain USB drop attack software. Some of people pick up these drives hoping to return them or claim a new device for free, insert them into their systems and just like that get into trouble. At this point, Cyber criminals are able to gain unrestricted access to their device or system, via USB drop attack softwares hidden within the mystery drives.
Reasons Cyber criminals attempt USB drop attacks
There are so many reasons for which Cyber criminals lunch USB drop attack on individuals and companies alike. Below are some reasons cyber criminals may seek to infiltrate your computer and other data storage devices include:
- To remotely take-over a victim's device.
- To spy on people using their webcam and microphone.
- To steal personal information and passwords.
- To access and encrypt a victims vital data and demand a ransom to release it.
- To erase, modify or inject malicious data and codes to or from a victim's device.
- To destroy target victims hardwares.
All these are motives that drive Cyber criminals, but the main drive is money. You may be familiar with the quote that "information is power' or 'knowledge is wealth". You'll find that this is a key multi-vator of cyber criminals.
Hence, they infiltrate a network, search for valuable information or dat, steal or encrypt it and then leverage the information either to the owner or to other interested persons in exchange for a ransom. This is why you must take pain to secure your data system and take steps as well as set up protocols to check-mate criminal activities. You must also ensure that you do not single handedly compromise our own system via our actions (i.e. by-cutting security protocols).
Part 2: What to Do If Data Lost After The Attack Happened?
If unfortunately, you've just experienced a USB drop attack, You may ask "what do I do?".
- First, turn off network access to terminate any ongoing data syphon.
- Restart your computer.
- Sweep through your computer for malware and viruses.
- Next, attempt to recover lost data following the steps below.
Method 01: Using CMD to Recover Data in USB
For Windows users:
Step 1:
- Type "cmd" and search.
- right-click on "cmd" option.
- Select "Run as administrator".
Step 2:
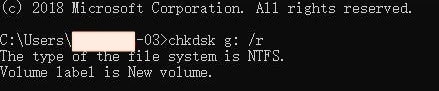
- Type "chkdsk g: /r"(g is the corrupted USB drive).
- Press "Enter".
The recovery process will begin promptly after.
For Mac users:
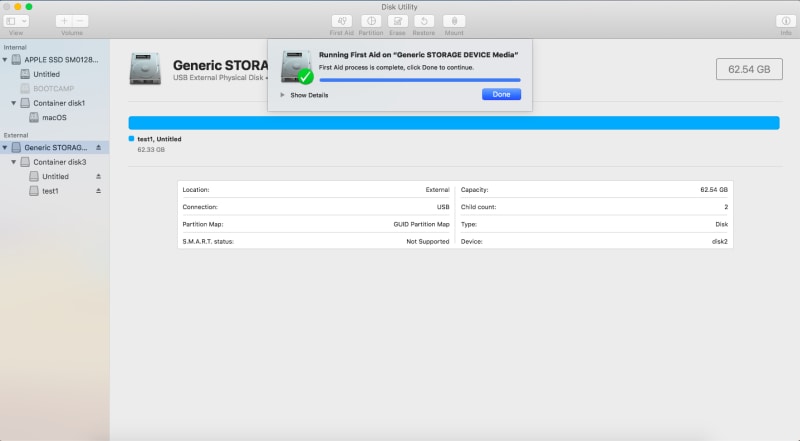
Note: Mac computers have an in-built troubleshooting tool called First Aid within Disk Utility. This can detect and repair damaged or corrupted USB drives.
Step 1:
- Open "Applications".
- Select "Drive Utility".
- Select target USB drive.
Step 2:
- Apply "First Aid" option from the top corner of the window and Run.
If successful the message "First Aid has successfully repaired the corrupted USB drive" will be displayed, else proceed to format the drive.
Method 2: Using Data Recovery Tool to Recover Data from USB
You may also choose to recover files from corrupted USB's using third-party data recovery programs. Here I recommend Wondershare Recoverit.
So how do you do this?
Before starting, you'll need:
- Your corrupted USB drive
- A computer (Windows or Mac)
- A compatible data recovery program for your computer (Wondershare Recoverit)
"Wondershare Recoverit" Data Recovery is suitable for both Windows and Mac and can used to recover photos, media files, documents and others from any formated or corrupted external storage device.
Step 1: Plug into the computer the corrupted USB drive.
Step 2: Download and Install Recoverit.
Step 3: Launch the program.
Step 4: Select target USB drive, Click "Next" (scan should proceed immediately, however, leave scan setting at default).

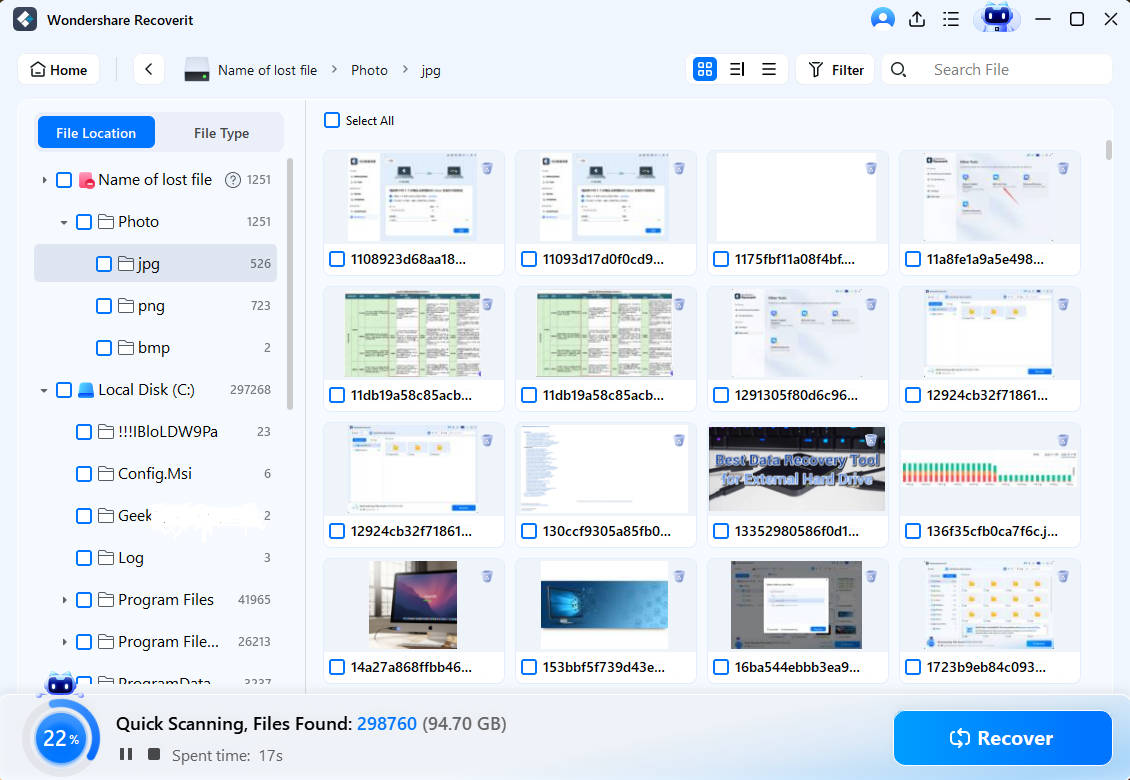
Step 5: Once the scan is completed preview results to Choose data you wish to restore. Click "Recover".
Part 3: Suggestions & Conclusion
So far you've known about USB drop attacks, their purpose and how to bounce back from an attack, the need to be cyber crime/security conscious and to avoid picking up mysterious USB drives. You also acquired that Wondershare Recoverit is a very important tool for recovering data lost or corrupted during the attack. Now, let's talk about how you can prevent USB drop attack.
How do you prevent USB drop attack?
- Ensure to keep personal, sensitive and work USB sticks separate.
- Avoid using strange or unfamiliar USB drives.
- Occasionally change your USB drives.
- Scan and encrypt your computers and USB drives regularly to ensure safety.
- Ensure to disable your computer's or PC's auto-run features.
- If you already have foreign USB drive plugged in: Quickly disconnect the Internet to prevent data upload or download. Next, restart your device immediately.
- Finally, ensure you participate and conduct Social Engineering Pen tests and training for you employees.
With the steps given above, you can actively work to prevent a potential USB drop attack and consequently protect your device and data from Cyber criminals. Next time when you find a USB falsh drive on the street or somewhere, just leave it out. Don't plug it into yout PC, so the malware will get no chance to attack your computer!
Stay safe and secure!
USB Solution
- Recover USB Drive
- Format USB Drive
- Fix/Repair USB Drive
- Know USB Drive











Theo Lucia
chief Editor